Read time: 10 minutes
Growing up in the era of the World Wide Web has opened up a wealth of opportunities, but it also comes with its downsides. Email accounts are inundated with spam, and computer viruses wreak havoc on business networks. As computer usage proliferates, individuals become more susceptible to cybercriminals and hackers, regardless of the operating system they employ—be it Windows, Mac OS, Linux, or Android.
Many individuals might lack the time or technical expertise to adequately secure their computers. The available information on computer security can often be perplexing and challenging to grasp. However, this need not be the case. We’ll outline the most effective methods to bolster your system’s security, both through manual techniques and utilizing a cutting-edge employee monitoring software solution.
7 Top ways to secure your PC
Today, we’re here to guide you through the most straightforward and effective methods to secure your computer.
Ensuring robust password security is paramount in preventing network intrusions. Passwords should be crafted with utmost security measures to minimize the risk of unauthorized access to your system.
For enhanced security, opt for longer, intricate passwords comprising a mix of numbers, letters, and symbols, with a minimum of eight characters. Short, easily guessable passwords can be cracked within minutes. Avoid using personal information like birthdays or easily identifiable phrases.
Allow us to guide you through the process of setting up your password on both Windows and Mac systems. Here are the steps you need to follow:
- To start with, tap on the Search button.
- Type up settings and tap on the Settings menu.
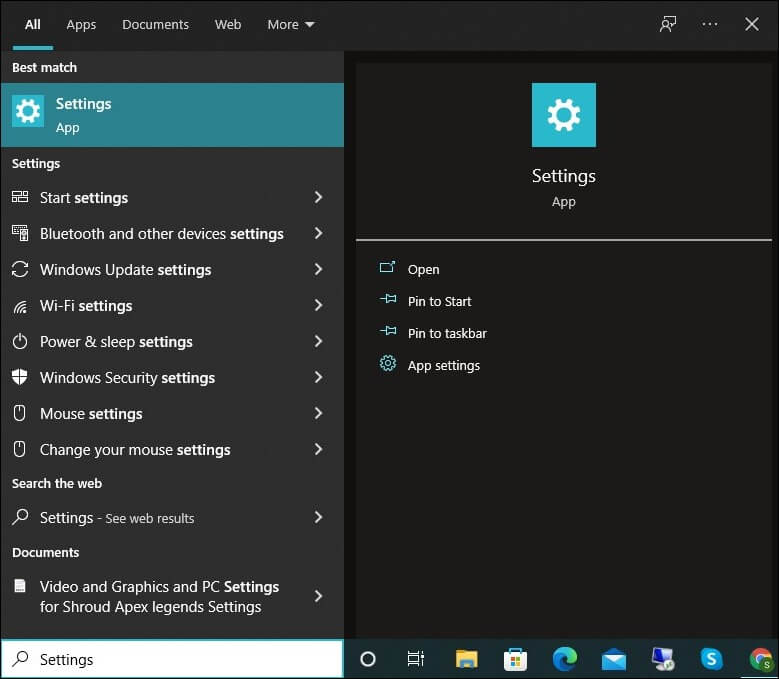
- Look for the tab Accounts and click on the tab Sign-in options.
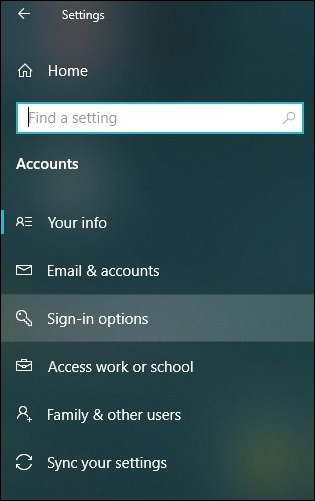
- Navigate to the right side of your window and tap on Password.
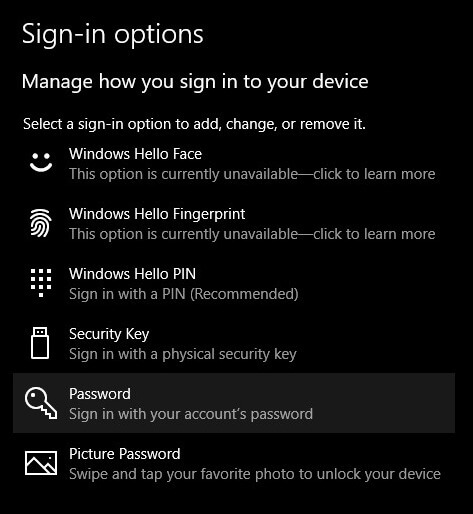
- Click on the Add button. If a password already exists, then you can modify it by clicking on the option Change.
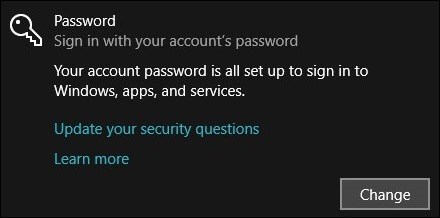
- Now you can type a new password with perfect combinations and tap on Next.
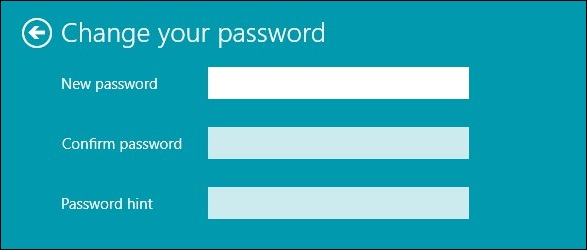
- Lastly, tap on Finish.
- Access the Apple menu and tap on System Preferences.
- Next, go to the tab General and tap on the Security and Privacy section.
- Click on the lock icon coming on the bottom of your window.
- If you are setting a password for the first time, click on the option Unlock.
- Checkmark the box Require Password and choose the period when your PC asks you to enter a password.
- Lastly, tap on the lock icon and save the changes.
Firewalls serve as security measures, scrutinizing incoming and outgoing network traffic. They act as a shield, warding off potentially harmful data from the internet. In essence, there are two main types of firewalls: Software and Hardware.
A hardware firewall is optimal for medium to large networks, whereas a software firewall suffices for small networks and individual PCs. For personal computers, installing a software firewall is advisable.
If you have accidentally or intentionally turned off your PC’s firewall, here’s how you can reactivate it:
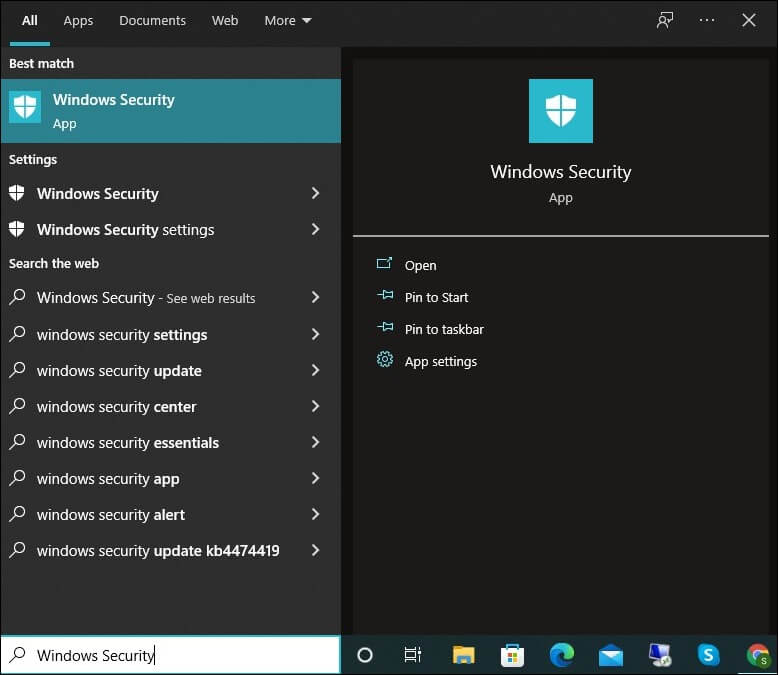
- To start with, tap on the Search button.
- Type Windows Security and tap on it.
- From the left side menu, tap on the tab Firewall and Network Protection. Three options will come up namely: Domain Network, Private Network, & Public Network.
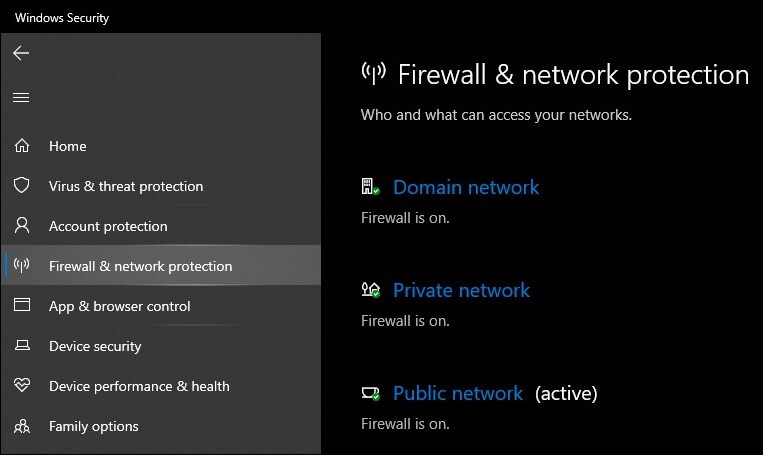
- Under these names, you can check the status of your firewall.
- To modify each network setting, you need to click on that network and turn it on or off as per your desired requirements.
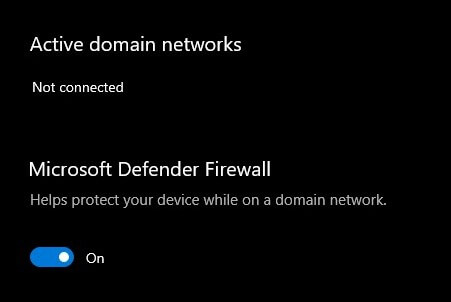
- Access the Apple menu and tap on System Preferences.
- Next, go to the tab General and tap on the Security and Privacy section.
- To enter your password, click on the lock icon at the bottom of the screen. Type in your password.
- The Firewall can be turned on (or off) once it’s unlocked.
- Lastly, tap on the lock icon and save the changes.
Ensuring your operating system and applications are up-to-date is crucial. Updates often contain vital security patches, safeguarding your data from potential interception or exploitation by hackers. Today’s web browsers are increasingly advanced, especially in terms of privacy and security features. Alongside browser updates, regularly review and optimize your browser’s security settings.
To enable automatic system updates, follow these steps:
- To start with, tap on the Search button.
- Type Settings and tap on the settings menu. Look for the tab Update and Security and click on it.
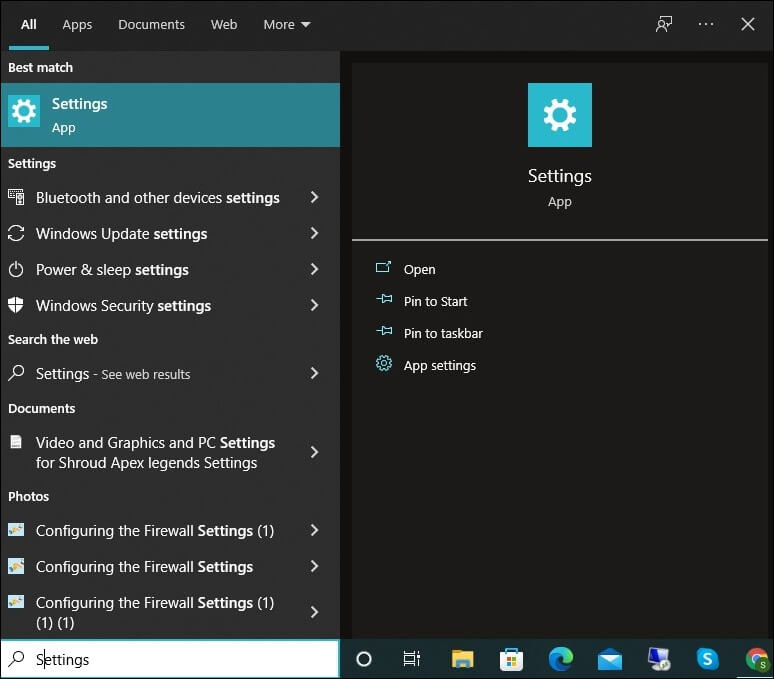
- Click on the option Windows Update.
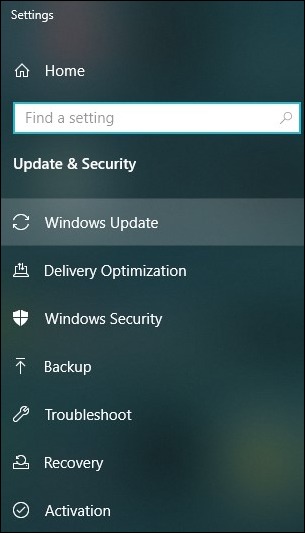
- Choose the Advanced options and then you can modify or update settings as per your needs.
- Access the Apple menu and tap on System Preferences.
- Tap on Software Update to check whether any updates are available or not. In case any update pops up, click on Update Now.
- Make sure the Automatically keep my Mac up to date option is checked if you want future updates installed automatically.
The initial line of defense against computer hackers involves using a password, yet augmenting this with a second layer significantly bolsters security. In tandem with your password, two-factor authentication (2FA) empowers you to input a numeric code dispatched to your designated phone number or email address during the login process. This robust approach to security effectively thwarts unauthorized access to your account.
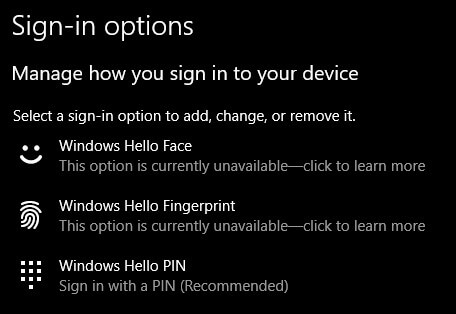
Moreover, Windows 10 provides a robust biometric authentication system known as Windows Hello, offering three distinct authentication methods: Windows Hello Face, Windows Hello Fingerprint, and Windows Hello PIN. Additionally, you have the option to seamlessly synchronize with password manager apps such as Keeper and Dashlane, further enhancing your security and convenience.
How to check whether your PC is compatible with Windows Hello:
- To start with, tap on the Search button.
- Type Settings and tap on the settings menu. Look for the tab Accounts and click on it.
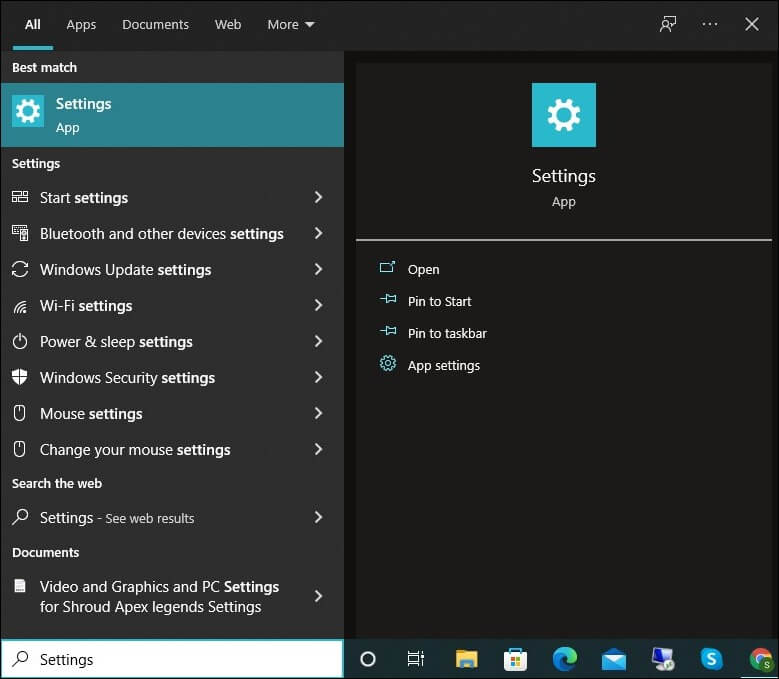
- From the left side dashboard, tap on the tab Sign-in options.
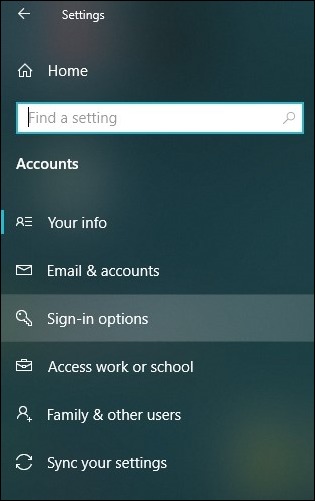
- On the right side of your window, you can check for Windows Hello. Tap on the desired password protection you want and set your security measures accordingly.
The internet is rife with computer viruses and malware, posing a constant threat to your system’s integrity. To safeguard your computer against unauthorized code or malicious software, utilizing reliable antivirus solutions like Panda Free Antivirus, Bitdefender, and Avast is imperative. While certain viruses manifest obvious symptoms such as slowing down your computer or deleting critical files, others operate more covertly, making their detection less straightforward.
Antivirus software plays a crucial role in safeguarding your system from real-time threats through its proactive detection capabilities. Top-tier antivirus programs also feature automatic updates, ensuring ongoing defense against the ever-evolving landscape of new viruses. It’s essential to not only install but also actively utilize your antivirus software. Regular virus scans should be conducted to maintain the continuous protection of your computer.
Microsoft Defender Offline is accessible to all Windows users, even if they haven’t installed Windows Security. This invaluable tool, Windows Defender Offline, specializes in identifying elusive threats like rootkits that often remain concealed within the operating system. By operating within a distinct, isolated environment, it ensures that evasive threats have nowhere to hide from the vigilant gaze of anti-malware scanners.
Starting with Windows 10 and continuing with Windows 11, Microsoft Defender Offline is seamlessly integrated into Windows Security, allowing you to initiate it directly from there. However, for users on older Windows versions, it’s necessary to download it as a standalone component.
Utilizing a Virtual Private Network (VPN) stands out as one of the most effective means to enhance your online security. When you route your internet traffic through a VPN, it undergoes encryption and is channeled through a server situated in a distinct geographical location. This process of masking your IP address effectively thwarts any attempts by your Internet Service Provider (ISP) to monitor your online activities.
Moreover, VPN users frequently have the flexibility to select server locations according to their specific requirements, whether it’s for unblocking geo-restricted content or ensuring speedy connections. Additionally, a VPN empowers you to access restricted or censored online material while maintaining secure browsing, even when connected to open Wi-Fi networks.
While these methods offer a strong foundation for enhancing your PC’s security, for those seeking an even more robust and user-friendly solution, consider Kernel Employee Desktop Live Viewer. This tool excels in automatically clearing outdated monitoring logs, comprehensively tracking your internet activities, and discreetly providing stealth monitoring capabilities. Additionally, it furnishes detailed insights into your email access, even in cases where a Secure Socket Layer (SSL) connection is not employed.
Furthermore, it boasts an array of advanced features, including its unique tracking capability, flexible monitoring scheduling, unified log recording, and an insightful report on accessed applications, among others. Notably, this versatile tool can concurrently monitor employee Skype chat conversations across an unlimited number of computers, solidifying its reputation as a dependable resource for maintaining top-tier system security.
Ending notes
While there are numerous methods available for bolstering your system’s security, many of them require a significant investment of time and expertise to implement effectively. This blog, however, focuses on presenting the most efficient and straightforward approaches to securing your PC in the least amount of time possible. It is our hope that you will find these methods practical and implement them to enhance your system’s security.
For continuous monitoring and tracking of your system’s activities, we recommend considering the Kernel Employee Desktop Live Viewer tool, which can further fortify your security measures. Notably, a demo version of this tool is accessible online for free, allowing you to explore its capabilities and maximize your layers of security and protection.







