Read time: 9 minutes
With increasing digitalization across every industry, we’ve seen an exponential increase in malware and ransomware attacks. These attackers have the education, healthcare, and government sectors as their primary focus for the ransomware attacks. 17% of the ransomware attacks used the STOP/DJVU ransomware to attack organizations, while the second-most used ransomware was the WannaCry encryption ransomware.
If you’ve recently lost your JPEG files to a DJVU ransomware attack, you must stay calm and avoid making impulsive decisions. We’ll guide you through the complete step-by-step recovery process of your JPEG files. We’ll explain in detail about the ransomware, how it infected your files and the steps to recover your data.
What exactly is ransomware?
Ransomware is a type of malware that blocks a user’s access to the data or threatens to make it public unless the user/victim agrees to pay a ransom. Often, attackers use a trojan disguised as a legitimate file that spreads quickly into the system and encrypts the files. The malware locks these files, which can only be accessed by decryption using the cryptographic key.
What is STOP/DJVU Ransomware?
DJVU ransomware belongs to the STOP family of ransomware. It was first observed around December 2018 and has been very actively attacking users all around the world. It comes in software crack packages, keygens, or adware bundles available on torrent sites or other platforms.
This ransomware encrypts your files using a single encryption key. The ransomware uses the key online if your PC is connected to the Internet. However, if the system cannot connect to their server, it uses an encryption key bundled in a malware code. In this case, the decryption of files is possible without paying a ransom.
Once the infected file is run, the trojan quickly spreads encryption malware in the background, infecting the system at a very fast pace. Main file types targeted are .doc, .pdf, .jpg, .jpeg, .mp4, and other popular file/application formats. The ransomware doesn’t encrypt the file completely, but only around 5 MB of it.
Once the malware encrypts the files, files are updated with .djvu extension or other similar extensions. Further, _openme.txt or _readme.txt files appear on the desktop. These files are basically ransom notes and contain details about the mode of payment and other such details. The virus also deletes disk backups, updates Windows registry entries, and updates various other system files, which makes it almost impossible to restore or recover the impacted data and files.
Example of Ransom note:
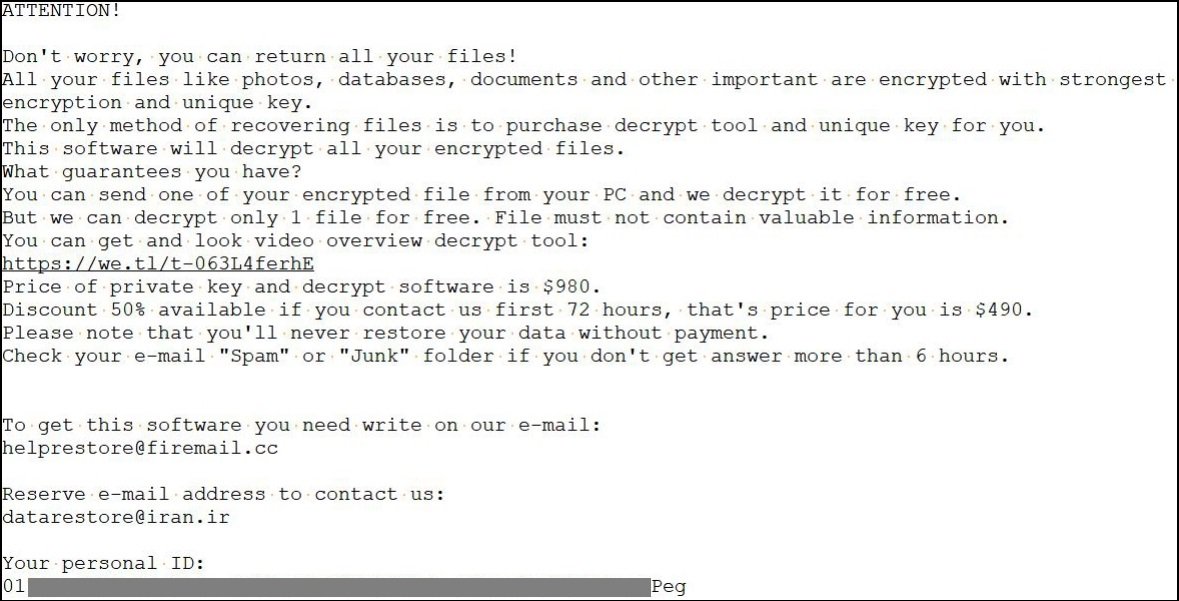
The virus also deletes disk backups, updates Windows registry entries, and updates various other system files, which makes it almost impossible to restore or recover the impacted data and files.
How did your files get infected by the STOP/DJVU ransomware?
Ransomware usually poses as legitimate files of several types, a harmful link on a website or an email, or a suspicious-looking advertisement. Once opened, this malicious software infiltrates the system rapidly and alters the important data. Read below to find out what could’ve led to your files getting infected by the DJVU software.
- Accessing unsafe links: Clicking on a suspicious link or advertisement is the most common reason for a ransomware attack. This link can be shared either via an email (phishing) or can be present on a website.
- Fake freeware: Downloading the crack version of software or keygens from unsafe websites often gives bundled ransomware access to infiltrate your system.
- Unsafe websites: Surfing unsafe websites often installs ransomware on your device without your knowledge.
- Fake extensions: Downloading extensions from unreliable websites can introduce different kinds of malware and ransomware in your system.
How to decrypt JPEG files affected by STOP/DJVU ransomware?
After outlining the basics of the JPEG ransomware and why it affects the files, we’ll be proceeding with the stepwise process of how to repair your JPEG files. Just make sure not to restore your files from a pre-existing backup (if any) to avoid losing it too. As long as the ransomware is in your system, the attackers will easily be able to encrypt the restored backup files as well. Also, do not pay ransom to the perpetrator, there’s no guarantee doing so will get you your files back.
Step 1. Isolate the corrupt device
Infections can stem from external storage devices and spread through the local network of your device. Hence, it’s crucial to disconnect the device from the internet and the storage to prevent it from spreading even further into the system. The steps to do this are:
- Open Control Panel and click on Network and Sharing Center.
- In Network and Sharing Center, click on the Change Adapter Settings option to see all the available network connections.
- Right-click on the network connections and click Disable to disconnect your system from the internet.
- Log out of any cloud storage account logged in your system and safely eject all the storage devices connected to prevent them from getting corrupted.
Step 2. Identify the type of ransomware
You need to search your system for SystemID.txt and PersonalID.txt files. These files are created by DJVU software and contain the encryption IDs used. You can find a reference to the personal ID in the _readme.txt file. All the offline keys end with a “t1”. If you can find these key files, it will be easier for you to recover your data and access your .jpeg and other infected files once again.
If you try to identify the ransomware by checking the file extension, try using the ID ransomware website. Just upload the ransom message and a random sample encrypted file, and it’ll provide you with all the details of the ransomware.
Step 3. Remove the ransomware files
It’s necessary to remove every single ransomware file present on your system to prevent it from infecting your files again. These malwares are highly efficient in storing their files in multiple places to reinstall their files even if you successfully remove it from your system. You can easily remove the ransomware from your device by first locating where all the files are stored and then removing it with the help of an antivirus.
You can even manually delete the ransomware by going to the paths given below and deleting files related to the ransomware. Just press Win + R on your keyboard and type these:
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
Step 4. Use a STOP/DJVU ransomware decrypt tool
After removing the ransomware successfully, use an online DJVU decryptor tool to recover data from the infected JPEG files. Just enter the Personal ID and the offline key in an online decryptor to recover your JPEG files. However, it’s impossible to decrypt your infected files without the offline decryption key. But you need to be extra careful while choosing the right STOP/DJVU ransomware decrypt tool to recover your files. Not all decryptors can successfully recover your data so research thoroughly and then make the choice.
Step 5. Check for data leak
Make sure that the attacker hasn’t stolen your data before encrypting it. Usually if that happens, it is mentioned in the ransom note with a demand of a hefty amount. Determine what data was stolen and inform the authorities as quickly as possible. Also, remember to comply with the GDPR guidelines to avoid facing any legal issues.
Step 6. Rebuild and restore your system
After removing the ransomware and decrypting your files, start afresh with a completely new Windows system. Doing so will guarantee that you don’t have any remaining files of the JPEG malware in your system. You can also restore your files from a pre-existing backup easily after rebuilding your system.
How to prevent a ransomware attack?
Now that we’ve a better understanding of the JPEG malware and the steps to recover data, let’s see some things to keep in mind to prevent a ransomware attack on our system.
- Antivirus protection: Install antivirus of a trusted brand on your system to detect harmful threats to your system.
- Security measures: Make sure that your system’s firewall is always enabled to protect your system from unauthorized access. You can also install a strong intrusion detection system to constantly check the system’s network traffic for any suspicious activity.
- Regular updates: Keep your system and its programs up to date to avoid facing any errors. Always download the updates from the official sites.
- Regular backups: Take regular backups of your essential data and make sure it can’t be altered once saved.
- Don’t click on suspicious links: Do not open links given on suspicious websites and do not open attachments in spam email messages. This can give direct malware access to your sensitive data.
Use a Professional Photo Repair Tool
If you are not able to find any personal ID or encryption keys mentioned in step 2, your system has probably been encrypted using online key(s). You may not be able to decrypt your files even with the help of expert decryption tools. But you can use the Photo Repair tool to get back your inaccessible and impacted JPEG files. It has the extraordinary capability to fix any kind of error occurring in the photos and major corruption issues as well.
Conclusion
Dealing with a ransomware attack can be challenging for anyone, especially if crucial data is involved. In this blog, you’ll find the basics of the STOP/DJVU ransomware and the stepwise process to recover data from infected files. DJVU decryptors are discussed to recover your files for free.
However, if you still can’t recover your files or the ransomware has left a significant amount of damage on your JPEG images. We suggest you use a Kernel Photo Repair tool. This tool can even repair corrupted JPEG files in no time and can be used to fix multiple files in one go.
FAQs
Ans. The most common malware used by perpetrators to attack individuals and organizations is the STOP/DJVU ransomware. This JPEG malware can critically damage important data if it’s not removed quickly.
Ans. Decryption is best suited for professionals to avoid causing more harm to your corrupt files. Emsisoft DJVU decryptor is one of the best online decryption software for ransomware elimination.
Ans. Run a full system scan with a trusted antivirus to check for any remaining ransomware file. The antivirus will locate the malicious file and remove it instantly.





![How to Repair Grainy Photos? [Instant Solutions]](https://www.nucleustechnologies.com/blog/wp-content/uploads/2020/02/fix-grainy-photos.jpg)
![[Top 4 Solutions] How to Repair Corrupt CR3 files?](https://www.nucleustechnologies.com/blog/wp-content/uploads/2020/10/1600x739-3.jpg)
![Easy Way to Restore Deleted Instagram Photos and Videos [Safely]](https://www.nucleustechnologies.com/blog/wp-content/uploads/2020/03/restore-deleted-and-lost-instagram-videos-photos.jpg)