Read time 4 minutes
The news about the latest massive CPU vulnerabilities – Meltdown and Spectre are around the corner since May 2017. As per Google Project Zero report, this issue affected processors of Intel, AMD, and ARM. These vulnerabilities caused serious security issues in CPUs that were released after the year 1995. They affected the processor performance, provided backdoors for hackers, and much more.
Till now, issues were reported in Intel, AMD, and ARM processors and there are three variants of the issue:
- Variant1: Spectre – bounds check bypass (CVE-2017-5753)
- Variant2: Spectre – branch target injection (CVE-2017-5715)
- Variant3: Meltdown – rogue data cache load (CVE-2017-5754)
Microsoft also has acknowledged these two vulnerabilities and has released several updates to help users mitigate them. According to Microsoft, they have taken the issue serious and have released patches for all the versions of Windows and cloud services offered by them. They also mentioned that they did not receive any information of attack from customers reporting these vulnerabilities.
The organization is working is working strictly with many industry partners such as chip makers, OEMs and application vendors to provide a secure platform for users. Hence, software updates are required for protecting hardware, firmware, and software.
Who is more vulnerable?
The two critical bugs – Meltdown and Spectre are CPU hardware bugs through which attackers can get a chance to steal your crucial data from the hard drive storage. The affected hardware chips and services are:
- Microprocessor chips manufactured by Intel, AMD, and ARM
- Devices installed with Windows operating systems such as laptops, computers, tablets, cloud servers, and smartphones.
- Devices installed with iOS, Android, Mac OS, Chrome.
Possible protections against Meltdown and Spectre:
There are many updates that are released by Microsoft to provide protection to all the users:
- Releases security advisory against the vulnerabilities
- Updates for Windows Operating systems, and web browsers (Edge and IE).
- Has released patches for protection of cloud services.
For detailed information about these vulnerabilities, read the following resources:
- Microsoft Security Advisory for Speculative Store Bypass: MSRC ADV180012 and CVE-2018-3639
- Microsoft Security Advisory for Rogue System Register Read: MSRC ADV180013 and CVE-2018-3640
- Security Research and Defense: Analysis and mitigation of speculative store bypass (CVE-2018-3639)
Actions to be taken to protect your Windows Devices:
We highly recommend all the users to take following measures to protect against these two vulnerabilities.
Action 1: Turn ON automatic updates to keep your Windows device up to date.
Action 2: Install your system with latest Windows security updates. In case, you have turned ON the automatic updates, check and verify if they are installed properly or not.
Action 3: Install the applicable hardware or firmware update that is offered by the device manufacturer. All the hardware updates are device manufacturer specific and can be installed from respective websites.
How will you verify that protections are enabled?
You can check for enabled protection with the help of PowerShell script published by Microsoft itself. The script can be executed easily on your systems.
Launch PowerShell as Administrator on your system and run the following commands:
Install the PowerShell Module
PS> Install-Module SpeculationControl
Run the PowerShell module to validate the protections are enabled
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuse
PS> Import-Module SpeculationControl
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy SaveExecutionPolicy -Scope Currentuser
If you find yourself stuck in such scenarios that are related to hardware and you’re unable to access your computer’s data, don’t fuss. Relax for a minute, think for possible solutions that can help in fixing such bugs. After you have fixed the bugs, use a professional third-party software to recover your data smoothly.
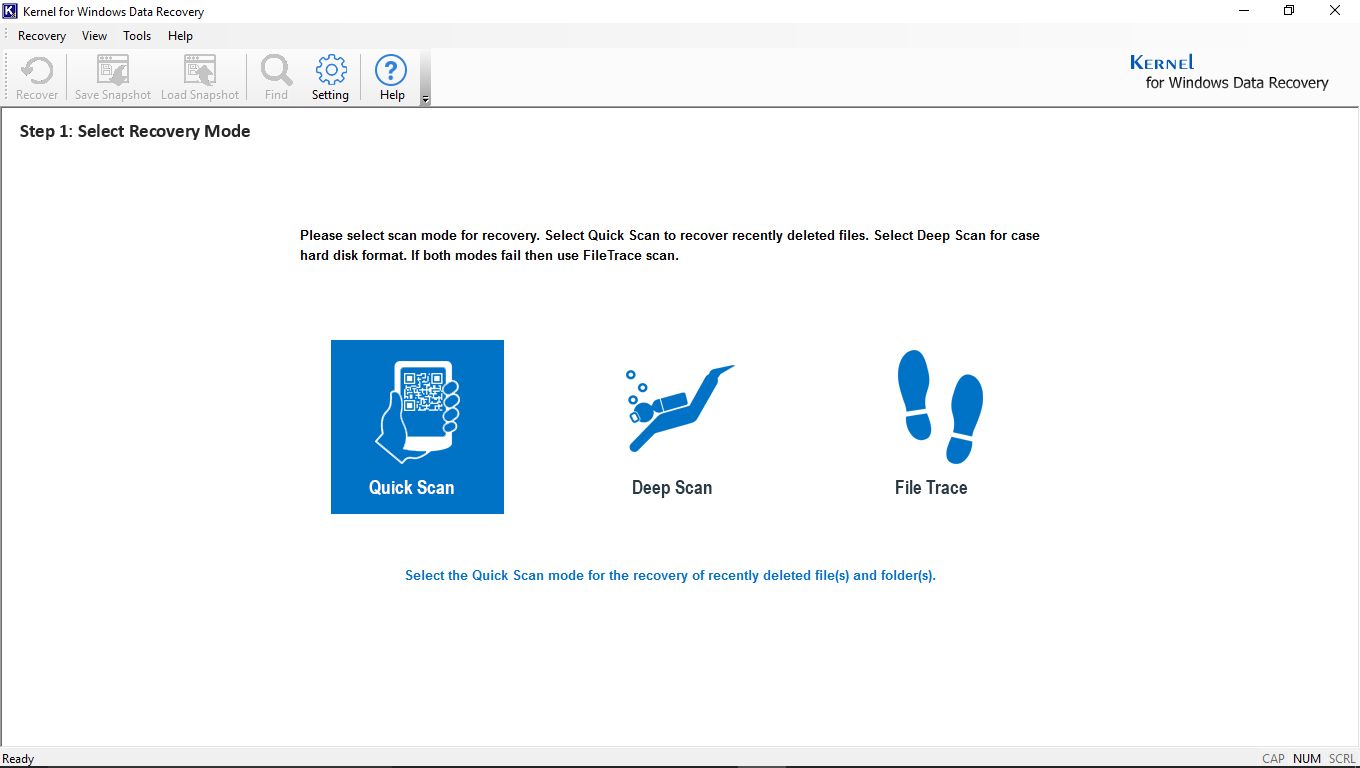
Automated third-party solution – Kernel for Windows Data Recovery Software
This is the most reliable and highly trusted software that is capable of recovering your Windows data. This Windows data recovery software works professionally to recover data after lost, damaged files, accidentally formatted HDD and corrupt HDD partitions. It can recover data from recycle bin folders as well. You can also recover from any external storage devices instantly with the help of this data recovery software.
Summary:
What will you do to save yourself from the two latest disclosed CPU vulnerabilities – Meltdown and Spectre. There are many emergency security advisories and patches available for these severe design flaws in modern CPUs.