WHAT IS lsass.exe AND HOW to Remove lsass.exe Files

Written By
Anju Chaudhary
Updated On
May 03, 2023
Read time 4 minutes
“Local Security Authority Subsystem Service file”, abbreviated as, “lsass.exe”, is an important part of Microsoft Windows’ Security policies like, Authority Domain Authentication (like authentication of password changes, login verifications etc.) and Active Directory Management on your PC. It is located in the folder, C:\Windows\System32. This file is never to be tempered with in any way like, edit, remove or delete and it exists at the sole location stated herein. In the present blog we are going to discuss about various aspects and scenarios of lsass.exe file.
As stated above, lsass.exe file is responsible for verification of validity of user login to your PC or server and generating process to authenticate users for the Winlogon service.
It is located solely in C:\Windows\System32 folder and nowhere else.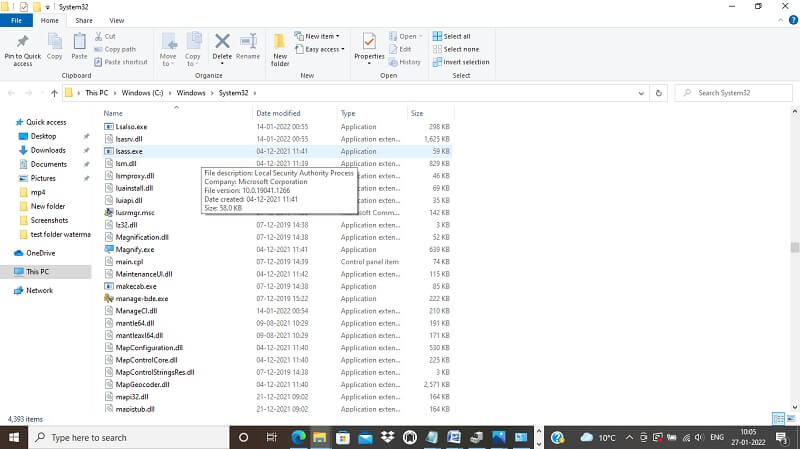
NO, lsass.exe is not a spyware. But, if any file with such name is present at any location other than C:\Windows\System32, then it is certainly a virus/spyware/Trojan or worm.
Further, lsass.exe file can become corrupt by virus or Trojan. Since this file is part of MS Windows, never delete or remove it, rather run antivirus program to remove virus.
From the following signs you can infer the presence of fake files:
You can use 3 factors to identify a fake lsass.exe file viz;
The one and only location where real lsass.exe file exists is C:\Windows\System32. If you find any such file anywhere other than this location like desktop, downloaded folders, on flash drive etc., then, the file is fake and can be dangerous and you should delete the same immediately.
Real lsass.exe is name consisting of all letters “LSASS.EXE”, in lowercase.
Files and processes with names similar to lsass.exe are fake files. Various variants of such similar named files can be as given below:
You can check whether the file is real or not, by copying the file name and pasting it anywhere like on notepad and convert the whole to lowercase to detect the real name.
Malicious software usually has much large size. ‘lsass.exe’ file in Windows 10 is 57KB and 47KB in Windows 8. If you find a much bigger file then, it is most probably fake file. Usually lsass.exe file uses less than 10MB of memory at any time but, it may increase in situations like;
To remove the fake lsass.exe files from your computer follow the steps given under:
You are also recommended to scan your PC using some efficient antivirus software and clean your system.
Read Also : Fix Windows 10 Error Code “0xc0000001”
In this blog we discussed what lsass.exe file is, its importance, functions and location. Further we discussed how imitate of this file can be a potent security threat/hazard to your PC. We have tried to guide our readers how to identify and get rid of such fake files and end security vulnerability of their PCs. Additionally, if you find any challenges with your Windows system and some files become corrupt, then you should use Kernel Windows Data Recovery software to recover complete files. It will recover all the data present in various drives excluding C drive where the software is installed.