Read time 8 minutes
The last few days were terrible for most of the Windows users, especially for those who were running the older versions like Windows XP and Windows Server 2003. Many of them were greeted by a message “Ooops, your important files are encrypted,” following which their systems became completely inaccessible. Victims were not able to restart the computer too.
It was the work of ransomware known by names like WannaCry, WCry, WanaCrypt, and WanaCrypt0r. It encrypted the data on the targeted systems and demanded $300 in Bitcoins as ransom from victims to decrypt their data. And within a few days of its first appearance, it became the largest attack of its kind. Later, the researchers were able to identify a kill switch to stop the ransomware from spreading. However, the damage has already been done worldwide.
Who is affected by the ransomware?
The latest reports on the WannaCry ransomware attack indicate that more than 10,000 enterprises and 2,30,000 computers from more than 150 countries including Russia, Ukraine, Taiwan, and Europe have been affected. Some of the early victims of this cryptoworm are:
- Telefonica, a Madrid based telecommunication and broadband company (Spain)
- National Health Service, Britain
- Renault, France (Automobile firm)
- Deutsche Bahn, Germany (Railway company)
- FedEx, US (Courier MNC)
WannaCry – how does it work?
The ransomware uses an exploit known as EternalBlue (earlier used by NSA and made public by some hackers known as The Shadow Brokers) to insert an executable code in the targeted system and also to distribute itself through the local network or the internet. Interestingly, Microsoft has released patches for this vulnerability by the security bulletin MS17-010.
As per the recent studies, WannaCry encrypts the files and documents and modifies their names by adding extensions like .wnry, .wcry, .wncry, and .wncryt. It is learned that it encrypts around 175 file types, mostly the commonly used file types, the Microsoft Office document files like word files, pdf files, excel files, etc. It enters the user system through various means, like malicious updates, links, unofficial websites to download tools, baits of no charge on software activation, channels with alluring offers, and more other ways which the user gets easily tricked off.
What makes WannaCry dangerous?
WannaCry makes use of inherent OS vulnerabilities to spread (instead of depending on user actions like clicking on links, downloading attachments etc.). Also, as per recent estimates, millions of computers use older versions of Windows and Windows Server, that too without applying the patches. The quick spread of this dangerous ransomware is attributed to these two factors.
How can you avoid the WannaCry attack?
Though the WannaCry Ransomware has been killed, it may reincarnate again without a kill switch. So it is better to eliminate all the vulnerabilities that it exploited. Some suggestions for this are:
- Replace older versions of Windows with newer versions if possible.
- Apply patches as recommended by Microsoft in the security bulletin MS17-010 (https://technet.microsoft.com/library/security/MS17-010)
- Disable SMBv1 port (https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1-smbv2-and-smbv3-in-windows-and-windows-server)
- Keep Antivirus and malware installed and updated on your system
- Do not click on untrusted links or visits unofficial websites often
- Use standard and official websites only to download software
- Keep your Windows Operating System updated for security patches
- Keep away from fascinating and fake offers unless ensured and satisfied
Do you need to pay ransom to decrypt your data?
Many analysts believe that the real motive behind the attack was not the ransom (as the sum demanded by hackers is very meager). In the malware, researchers have not been able to identify codes that could be used to identify those who pay the ransom, to decrypt the files, or to delete the encrypted files. As per various reports, the hackers have been able to raise only a meager sum from victims, showcasing the lack of credibility in the decryption promise. Also, there are no reports on confirmed decryption of data after the payment of ransom. Considering all these facts, it is better you restrain from paying the ransom.
How to minimize the impact of the WannaCry ransomware attack?
What are the most reliable options for the ransomware attack victims to retrieve their locked data? You can do many things to minimize the impact of a deadly ransomware attack. Here is what you can do:
- Desist from paying the ransom (as there is no guarantee of recovery)
- Isolate the affected computer from the network (to avoid the spread of the ransomware)
- Disconnect the internet from the affected computer
- Take precautions against further ransomware attacks (use latest OS versions, update patches, & use antivirus programs on unaffected computers)
- Use internet with maximum precaution (be vigilant against phishing mails & untrusted links)
- Recover the lost data from backups if backups are available
Can Windows recovery tools help you get back the inaccessible data?
Frankly, tools cannot decrypt the files encrypted by the WannaCry ransomware. However, they can help you deal with the data inaccessibility situation in different ways.
Some studies indicate that it is possible to recover the original unencrypted data deleted by WannaCry using the deleted item recovery feature a good Windows data recovery tool. This is a distinct possibility, as the WannaCry virus doesn’t overwrite the deleted data in most locations (except desktop, documents, and removable devices). Also, it is understood that the WannaCry software encrypts only about 175 file types. So if the data is of a different file type, the chances of recovery are very high.
Alternately, one can try to restore the entire data from the affected system to a different system using a Windows recovery tool, and then attempt to decrypt them using some data decryption tools.
However, the success of all these recoveries depends on many factors like the type of the file, location of the data, possibility of overwriting the deleted data, etc. And most of the WannaCry victims prefer trying these methods overpaying the ransom.
Restoring inaccessible data using the software
To restore the data from the affected computer, you need to install Kernel for Windows Data Recovery on a new computer (preferably with a new version of Windows OS). Now connect the hard disk of the affected computer to it, and follow the steps below to scan the affected hard disk using software.
Step 1. Launch the application (from the Windows Start menu), and select the File Trace mode.
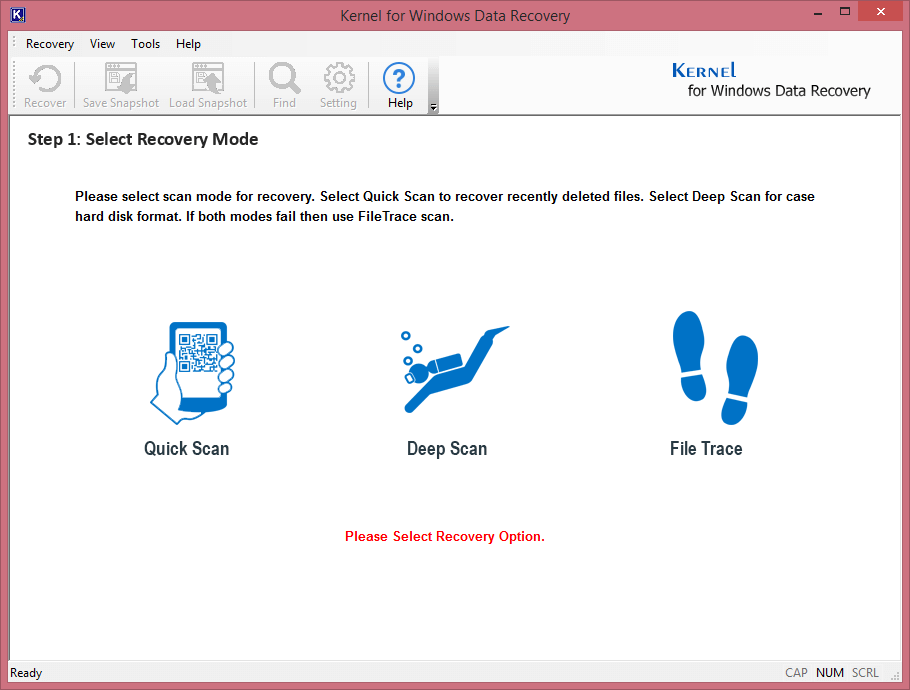
Step 2. Select the affected hard disk (which will be displayed on the left panel). You can view the details of the hard disk on the right panel. Click Next.
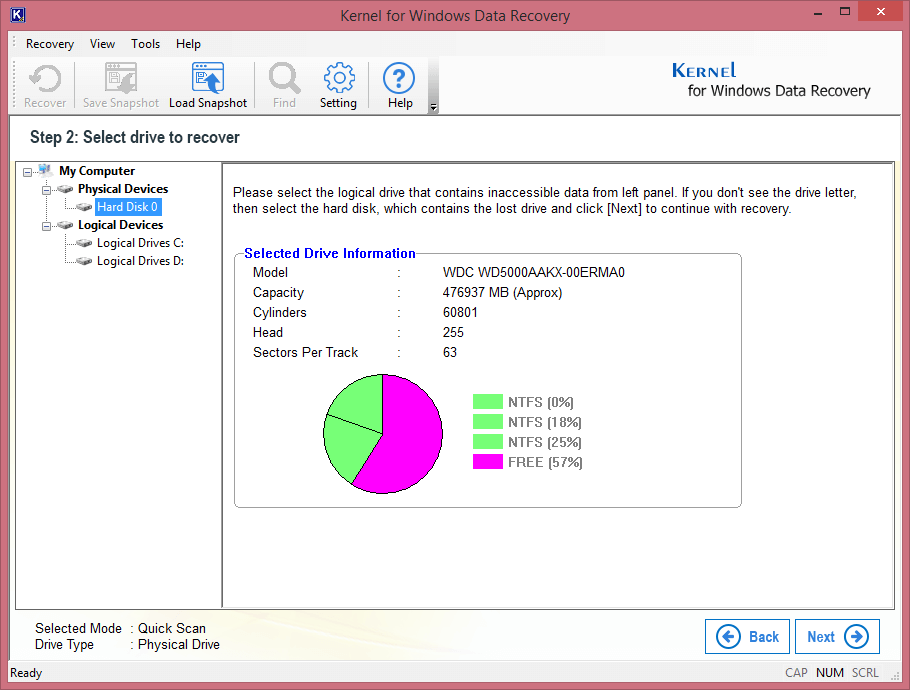
Step 3. Select Use existing partition info and click OK.
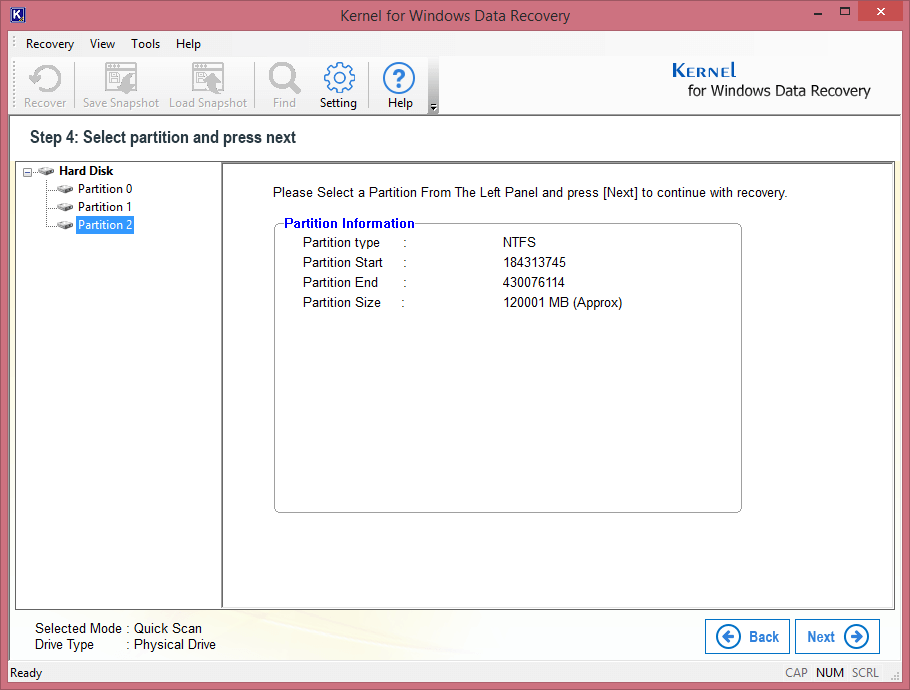
Step 4. Now, select the partition to be recovered and click Next.
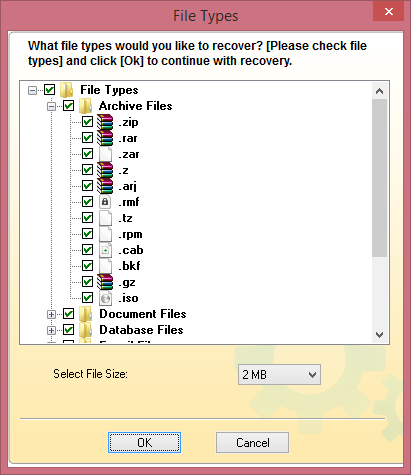
Step 5. Select the file types you want to recover. Click OK.
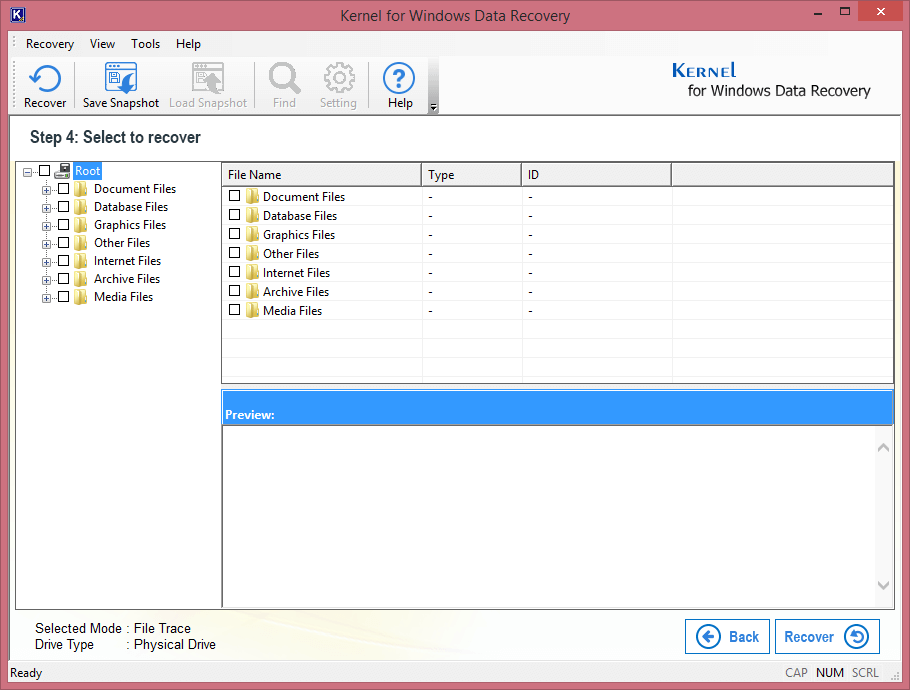
Step 6. When the Windows data is displayed, select the file you want to preview.
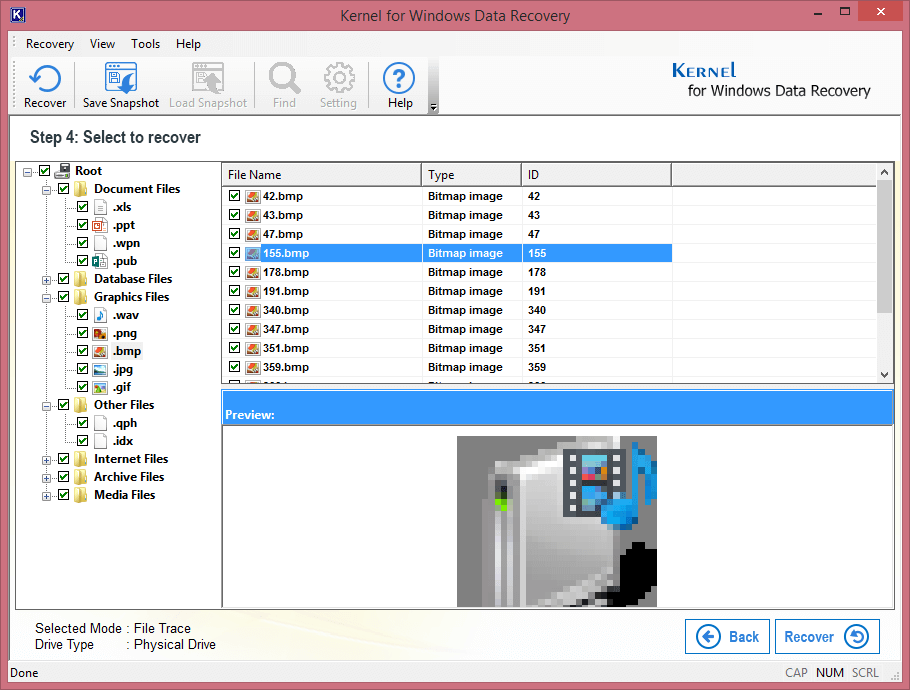
Step 7. Specify the exact files you want to save. Click Recover.
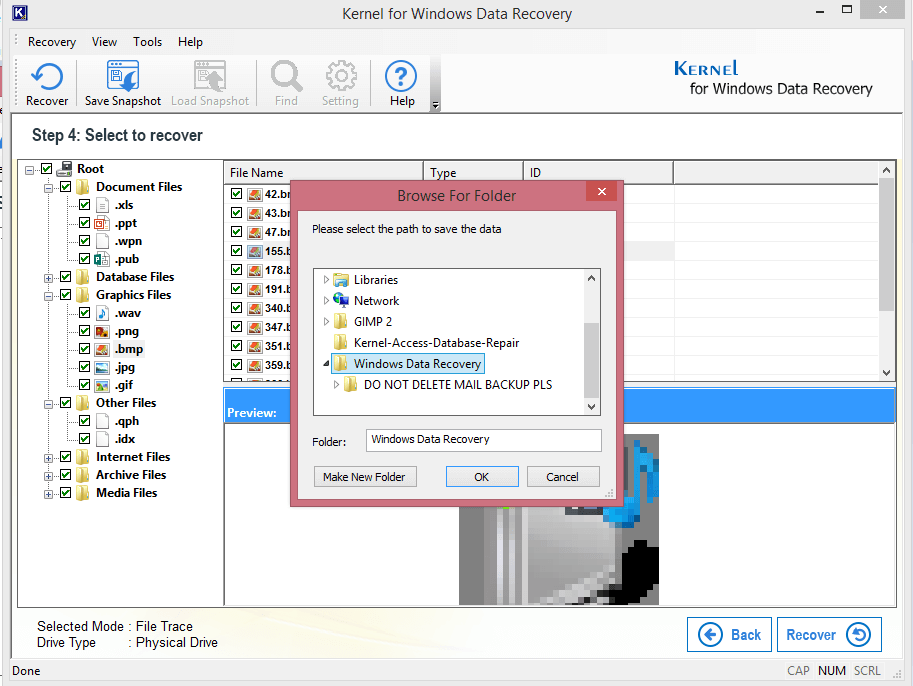
Step 8. Now, browse for the saving destination. Click OK.
Step 9. Finally, click OK when the saving is complete.
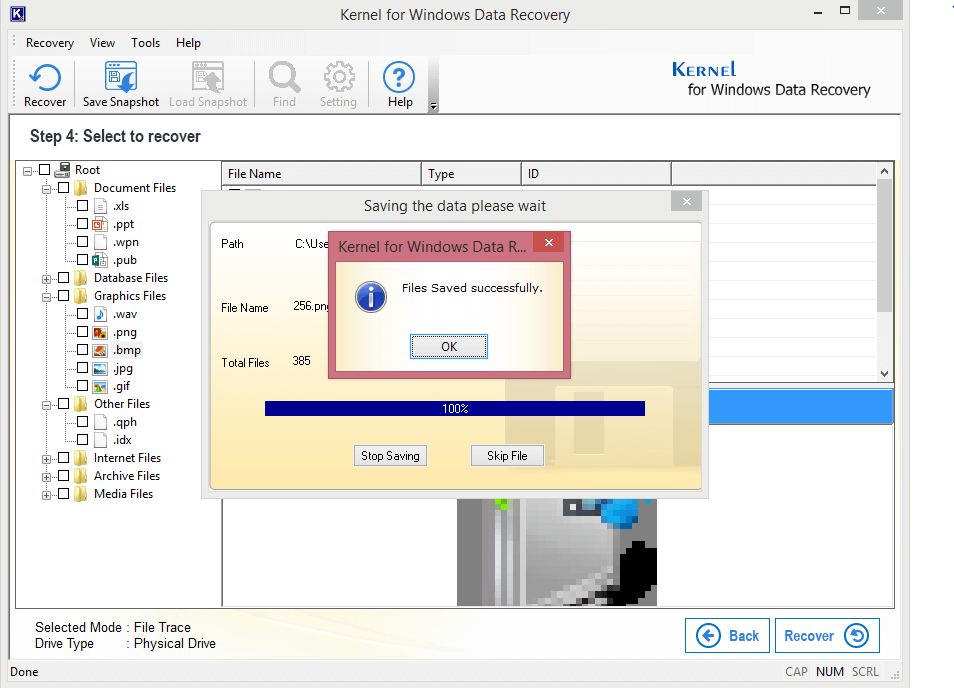
Note: If some data is left in encrypted state even after the recovery, you may try some decryption tools.
Conclusion
We got a good idea of the WannaCry ransomware impact globally, its harmful effects, some helpful prevention measures, working of the ransomware, ways to minimize the impact of WannaCry, and at the end, an aid to users in the form of a smart tool to recover and restore corrupt and inaccessible data from Windows drives efficiently.








