Read time 7 minutes
A computer has only a limited storage capacity to store the files. The user divides the whole disk space into various drives for better management and saves the data in multiple folders in those drives. We also know that it is not suitable for an unnecessary file to remain in the drive for an unlimited time, wasting the precious storage space. So, we delete the older files regularly. After the deletion of the file, the storage space becomes available for a new file.
An average user feels that the deletion of the file is enough to destroy the data permanently. But there are several recovery tools that can recover the deleted items from the hard drive even after the drive is formatted, and a new operating system is installed. It forces the user to look for another deletion method called shredding. A clear difference between a normal deletion and shredding is that during the deletion, the storage space is cleared, and the reference point is also deleted. But an efficient recovery software can quickly recover the file. However, the shredding action not only removes the data and the reference point, but also overwrites the file with some random information.
So, if you want to get more storage space for new information, file deletion of data is enough. But if you want to ensure that the data of a deleted file is irrecoverable, you need to shred the file.
A file recovered after the shredding will be unusable even after the recovery. If you want to completely delete any file from the computer that has some crucial business information related to your business, then you can employ a third-party shredding application. The application should use trusted algorithms and erasure methods to delete the file completely.
- DoD 5220
The DoD 5220 (5220.22-M) was developed by the Defense Security Service (DSS) of the Department of Defense. The standard process includes three secure overwriting methods to replace the data in a selected file. In the first method, the algorithm overwrites the addressable location in the file with binary zeroes. Similarly, the second method overwrites the addressable location in the file with binary ones. The third method overwrites the addressable location in the file with the random patterns. - US Army AR 380-19
US Army AR 380-19 is another data sanitization algorithm that shreds the file by overwriting its information beyond recovery. It is such an efficient method that after using the US Army AR 380-19 sanitization method, the file will not be recoverable by any professional recovery software. The data sanitization method works in three passes – in the first pass, it writes the random character to the file; in the second pass, it writes the selected character (e.g., 0 or 1), and in the third pass, it inputs the complement of the selected character. Later, it verifies the result of the sanitization method. - Gutmann Method
Gutmann’s method is an erasing algorithm developed by Peter Gutmann; it runs a series of 35 patterns to the area of the file that you want to delete completely. The method does not use 0 to replace the data but uses various random characters.These shredding algorithms are widely used by defense establishments and research organizations to secure their confidential data. Also, there are many other shredding algorithms used by different industries to ensure that their data is safe always.
These are some important shredding algorithms that a professional shredding software should use to ensure that the data is deleted completely. The majority of the shredding software uses a single shredding algorithm to delete the data. But there is one software called Kernel File Shredder that lets you choose a significant number of algorithms. You can select the file and select any suitable algorithm to shred and delete the files.
Kernel File Shredder
Kernel File Shredder lets you choose multiple files at a single time and shred them after selecting the algorithm.
- Start the software and go to the Options tab on the left-hand side.
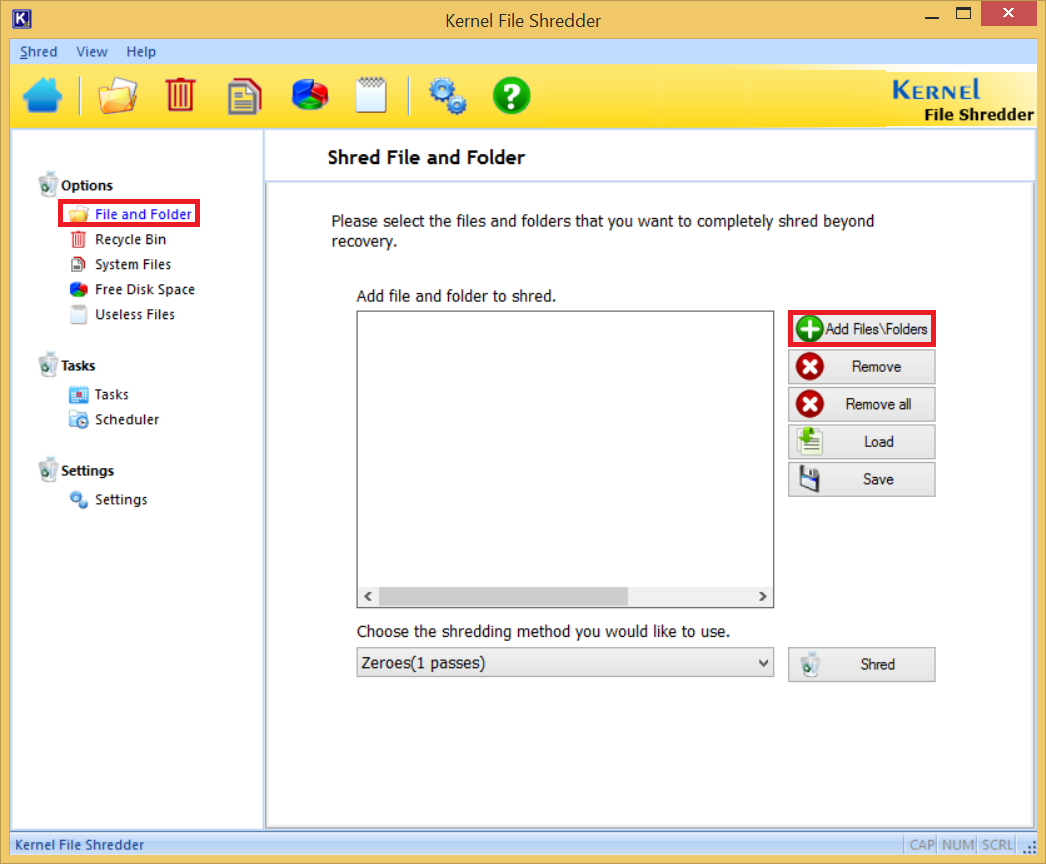
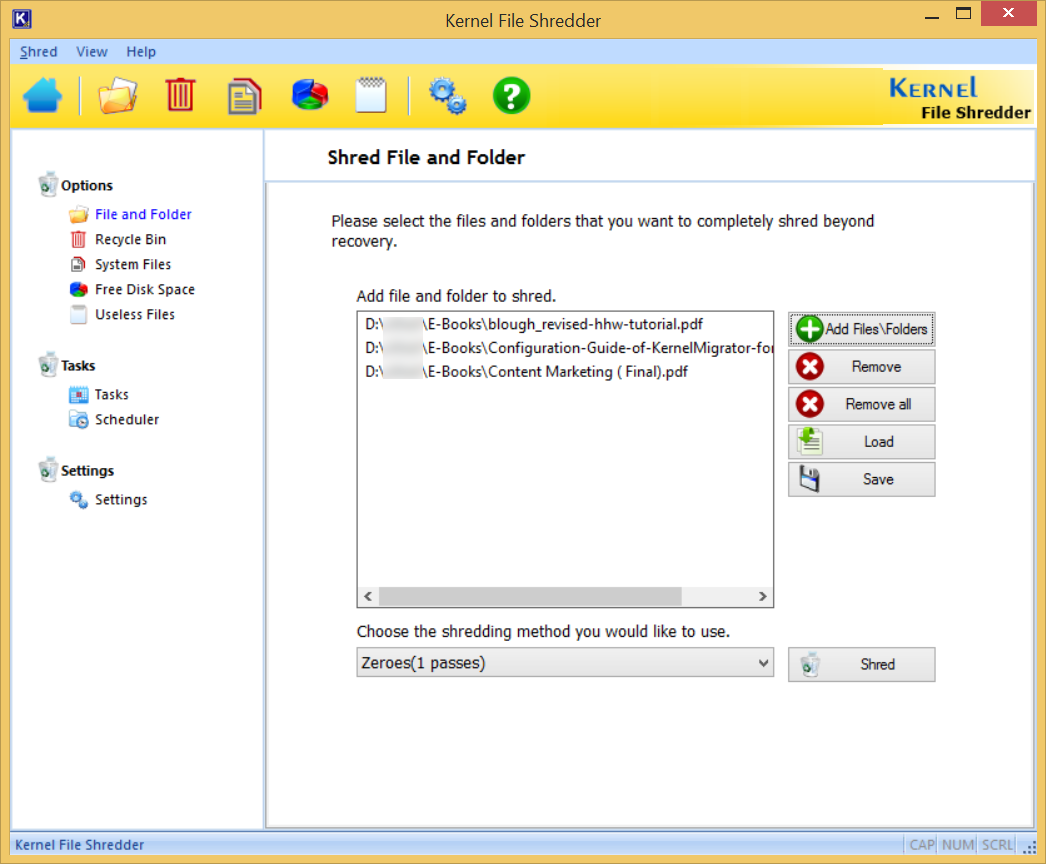
- Click File and Folder that will open the wizard to shred file and folder. Click Add File\Folders.
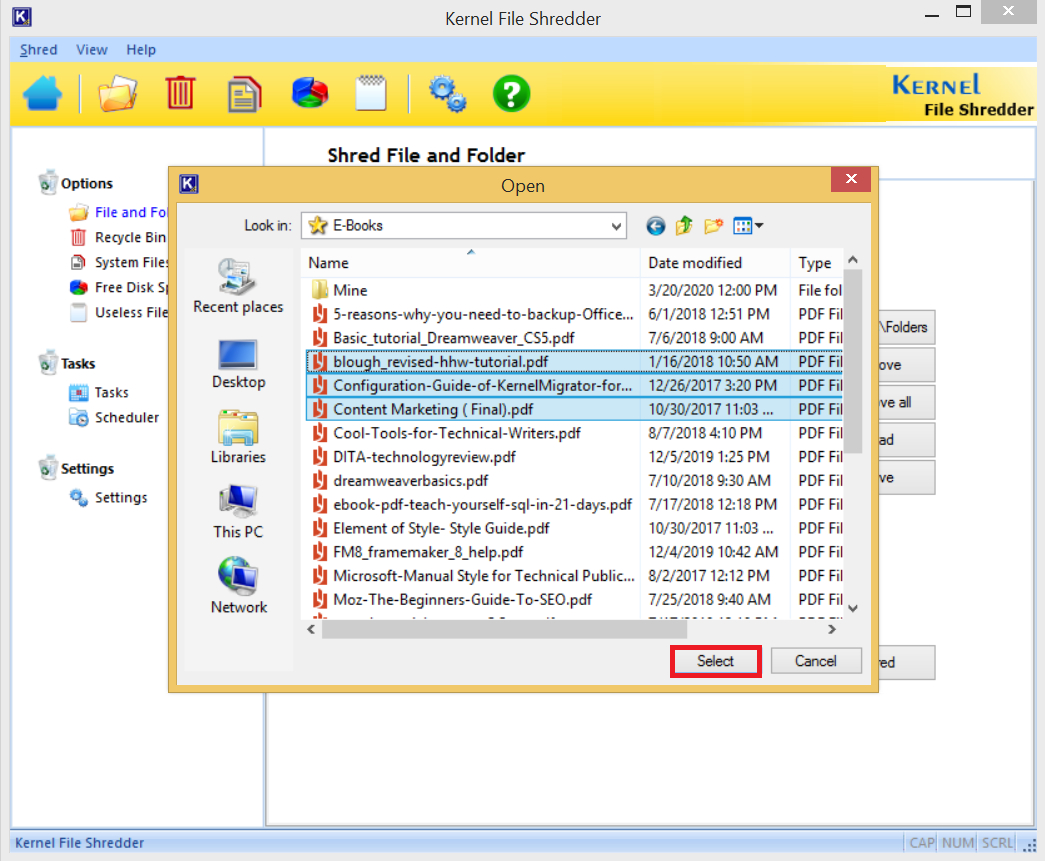
- Choose the data that you want to delete permanently. Then click Select.
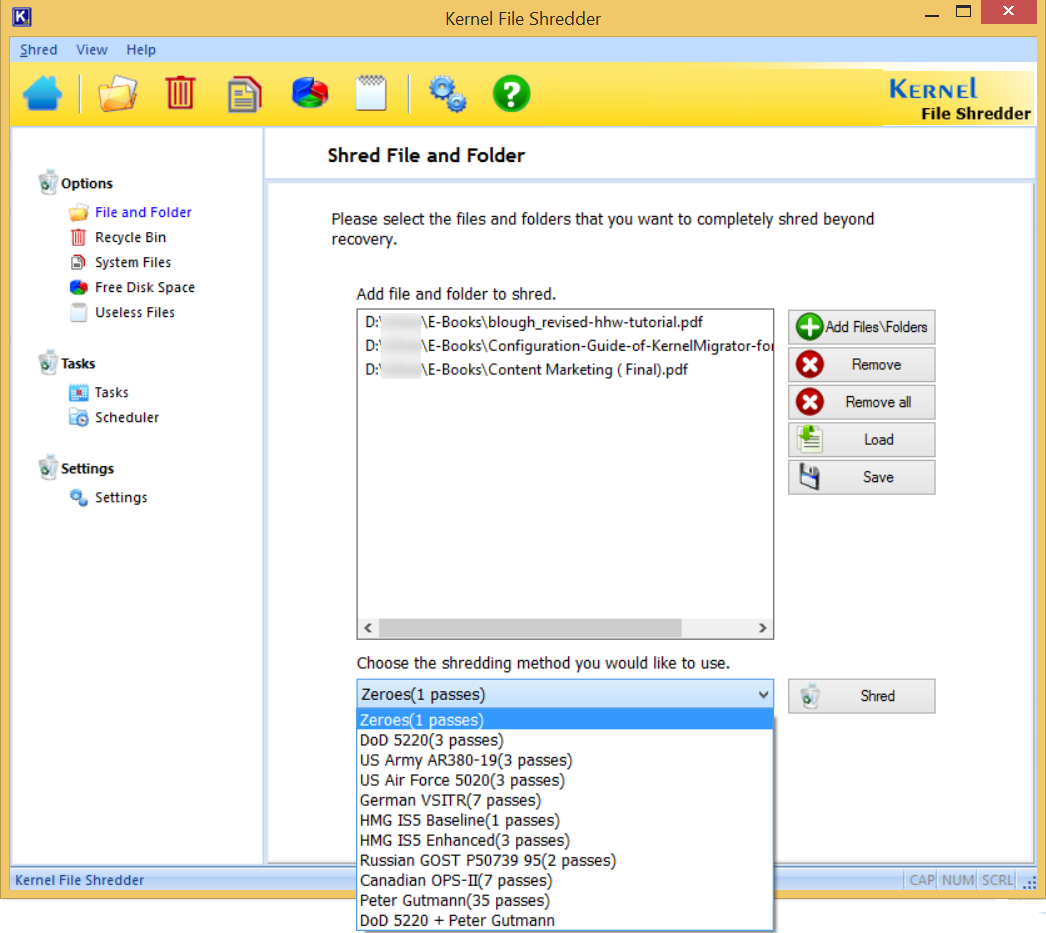
- After the selection of the files, your next step is to choose the shredding algorithm.
- There are 11 types of shredding algorithms available for your selection. Choose anyone.
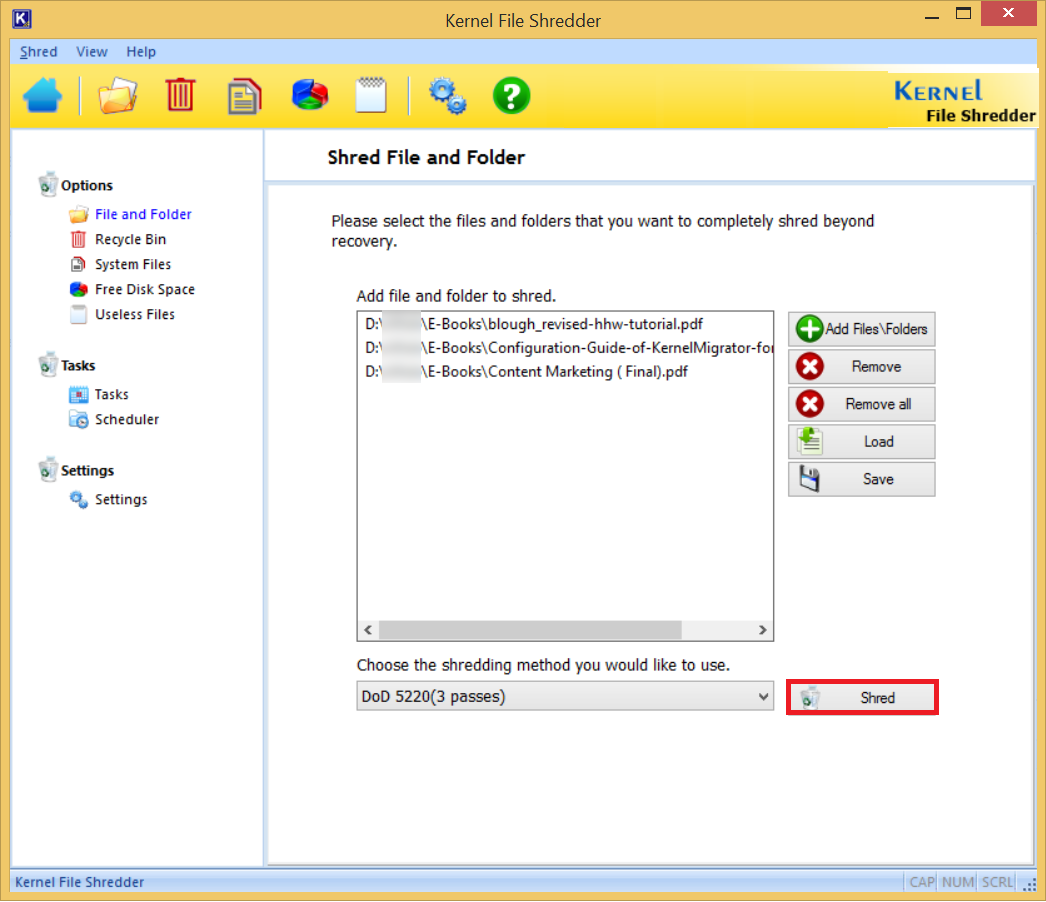
- After choosing the algorithm, click Shred.
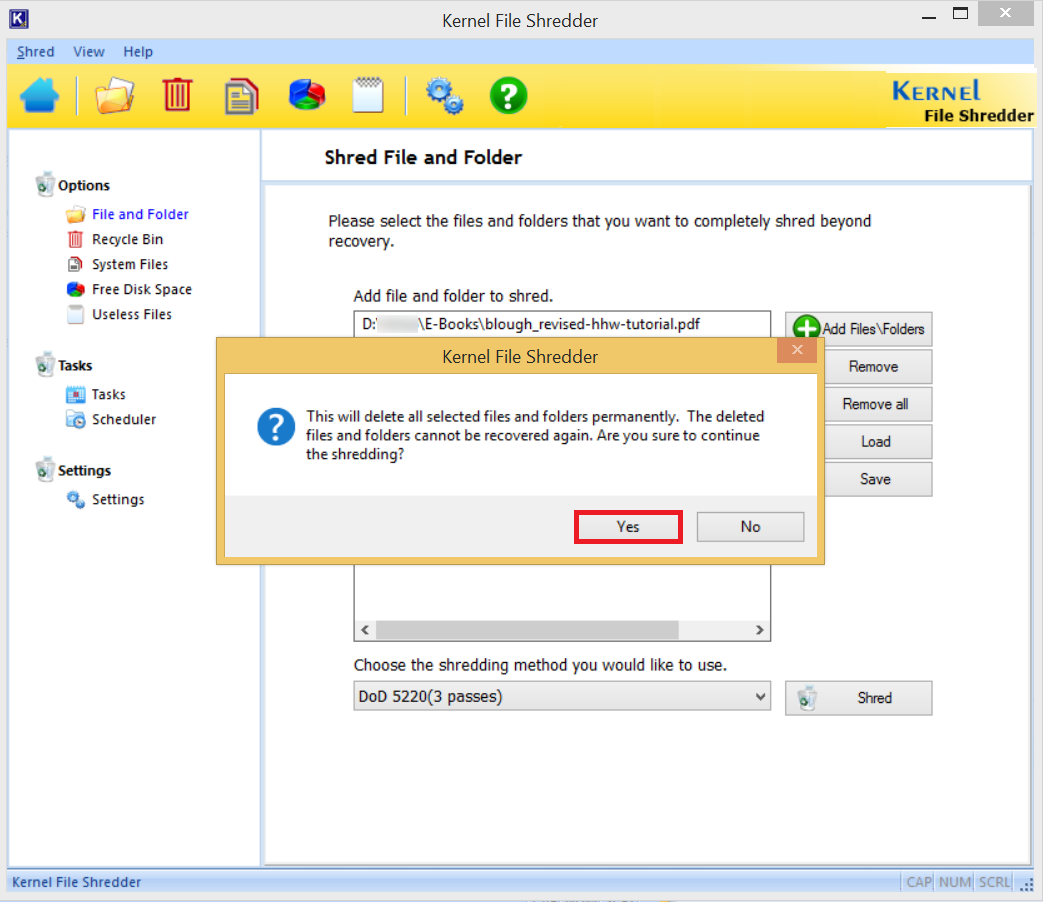
- A message will inform you that it will delete all selected files and folders permanently. The deleted files and folder cannot be recovered again. Click Yes.
- The tool has shredded all the files permanently. Click OK.
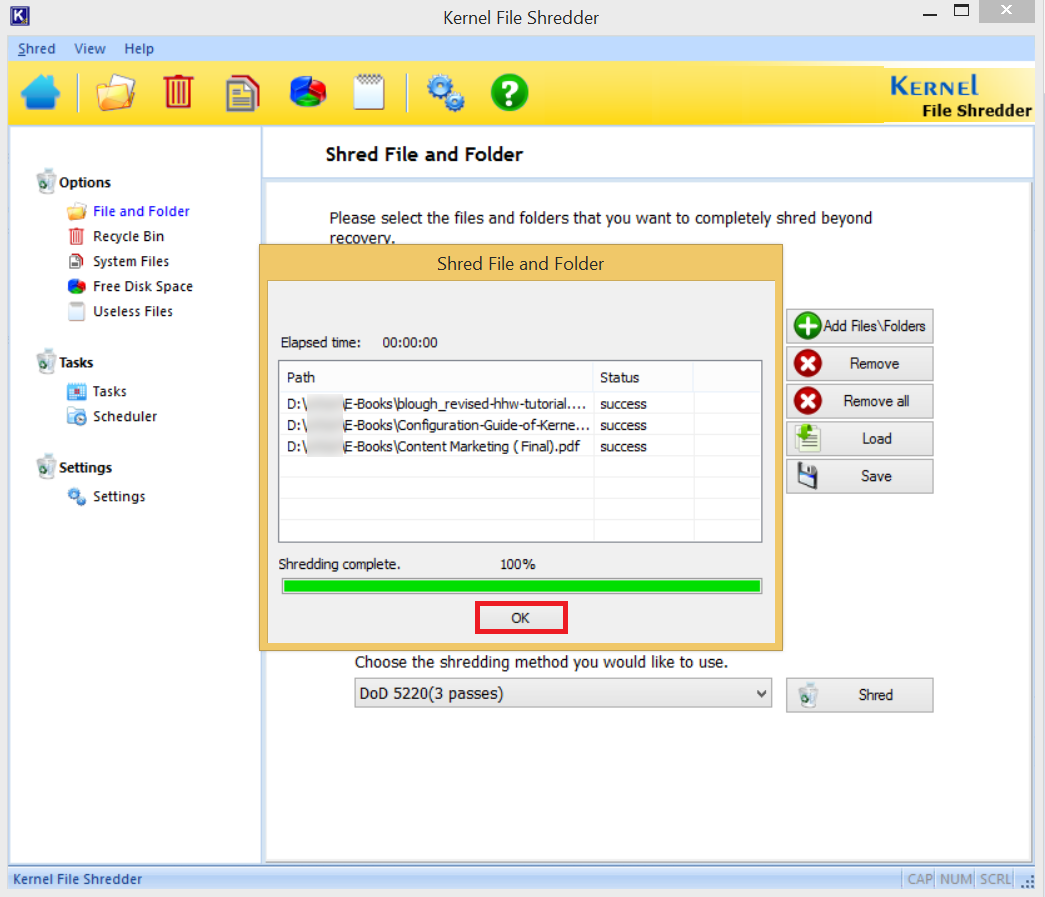
Kernel File Shredder has multiple shredding options like:
- Shred files from Recycle Bin
- Shred System Files
- Shred Free Disk Space
- Shred Useless Files
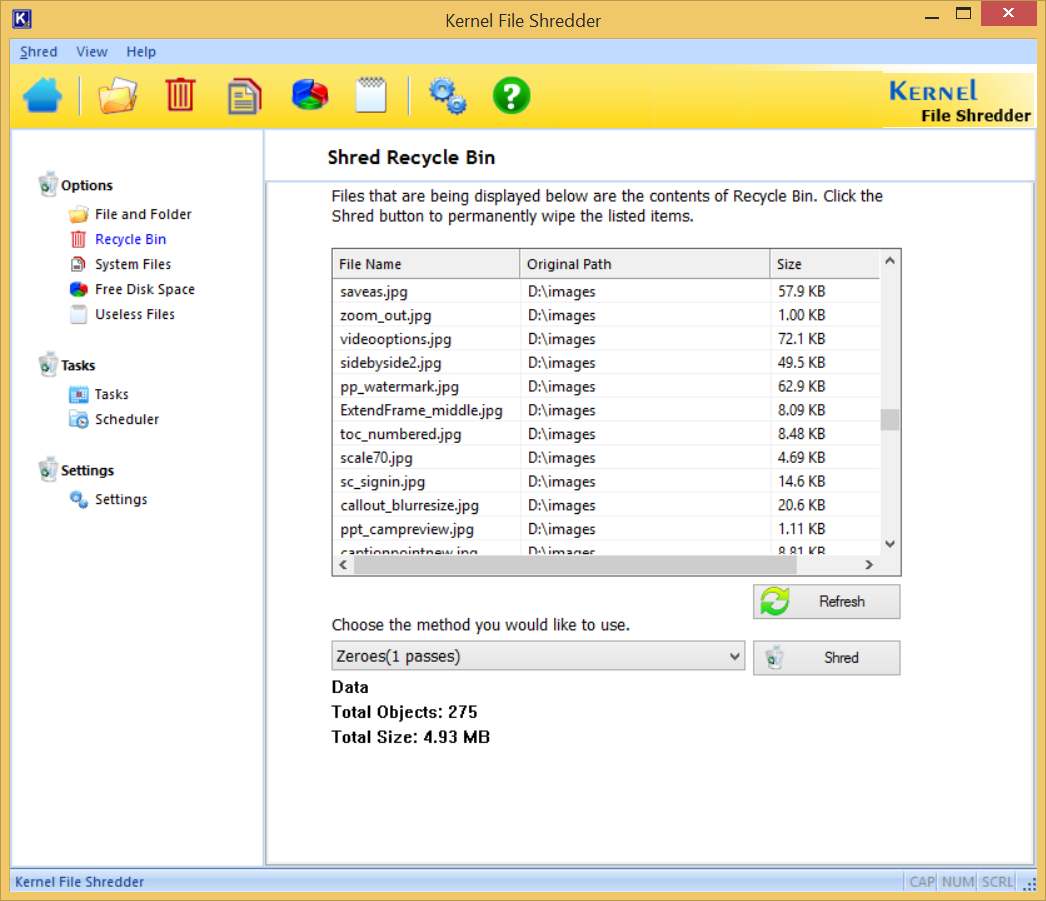
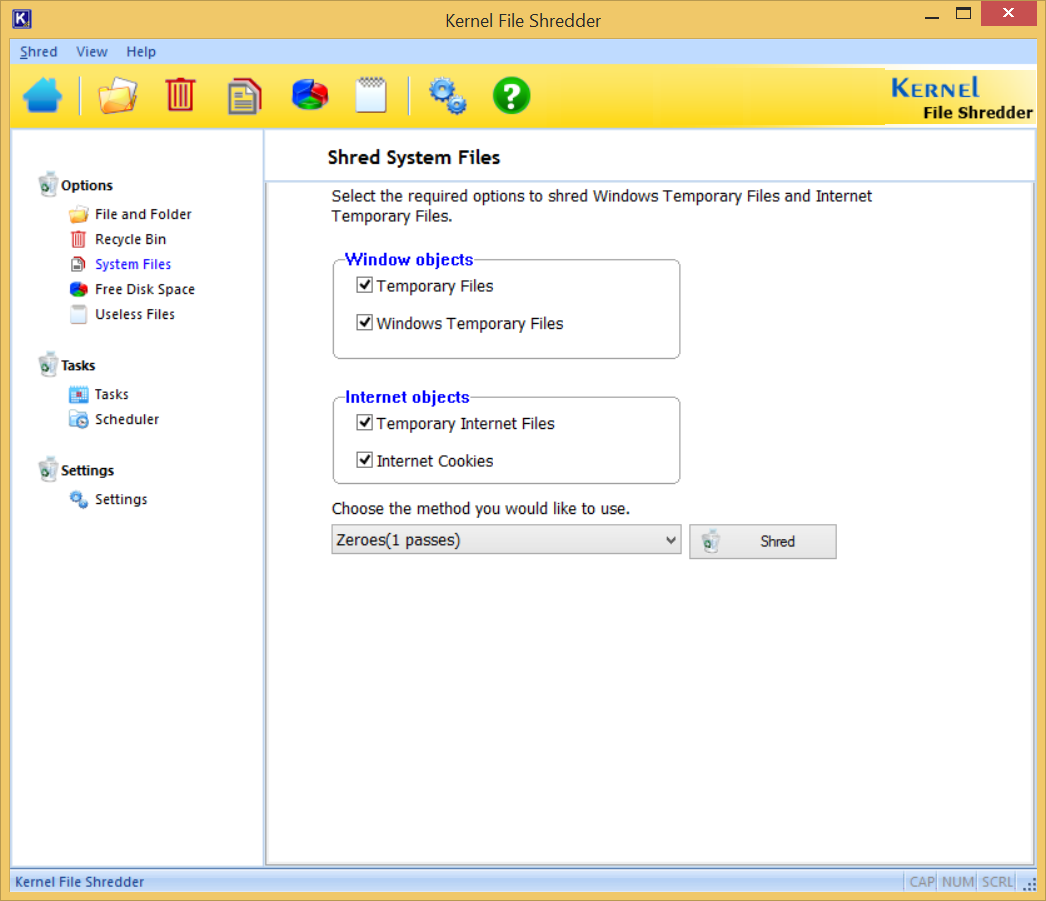
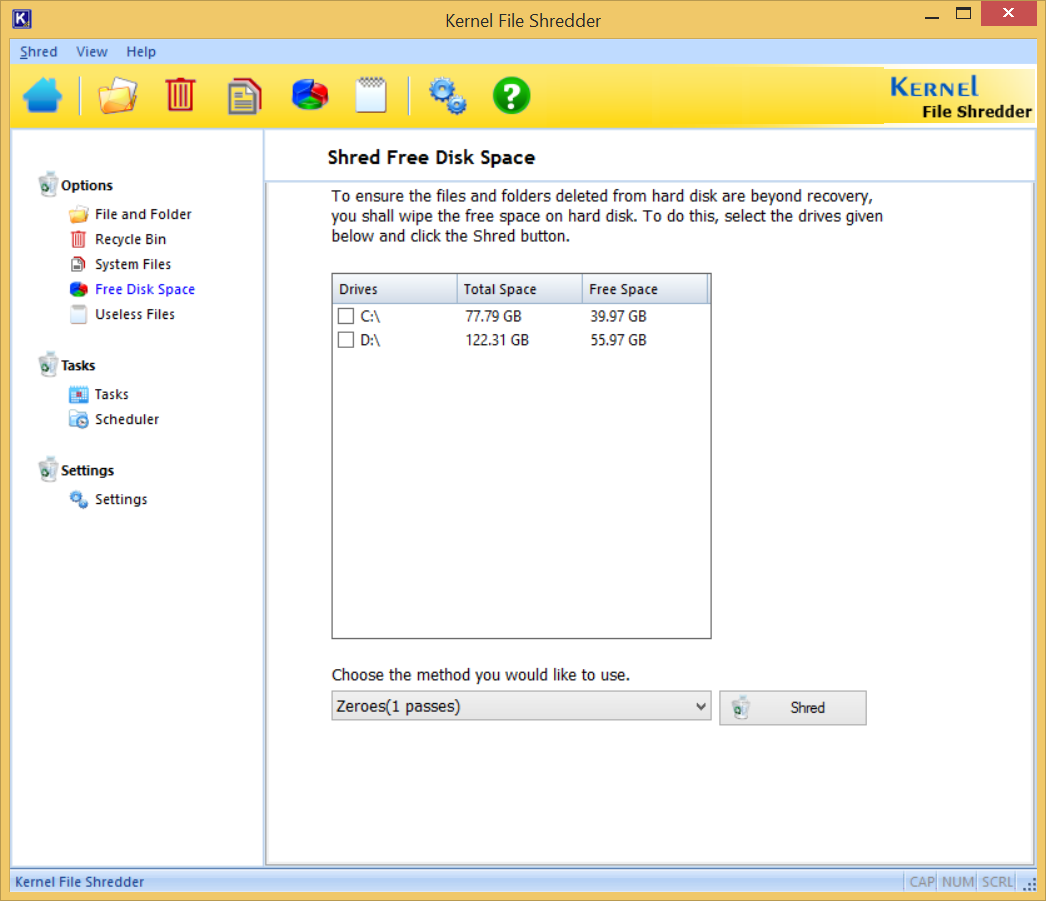
Conclusion
A business has a lot of valuable information that is old and can be deleted. However, it would not like to lose this data to any other person. So, shredding is a better option than the deletion, and Kernel File Shredder will do it correctly. Any data recovery tool will not be able to find the files ever after scanning the whole drive many times.